Cyber Security Services
Recognised as one of the leaders in Singapore cyber security, Entrust Network offers an array of cyber security consulting services and oversees the administration of established policies, enabling your organization to cultivate and uphold the cyber capability essential for achieving success.
Capabilities
Our cyber security risk management services enable you to see more in order to protect your organization.
How we can help.
As technology rapidly evolves and digital adoption accelerates, securing your business infrastructure and data has never been more crucial. From ransomware and viruses to phishing campaigns, the frequency of attacks has surged exponentially over the last decade, with no indications of a decline.
As a leader in managed service provider cyber security, our proactive approach includes vulnerability assessment Singapore, ongoing monitoring, analysis of threat intelligence, and swift incident response. This comprehensive approach is designed to guarantee real-time protection against the ever-evolving landscape of cyber threats.
Get started working with true experts in the industry.
Entrust Network has been supporting SMEs since 2006. Let us become a part of your team.
WHY US
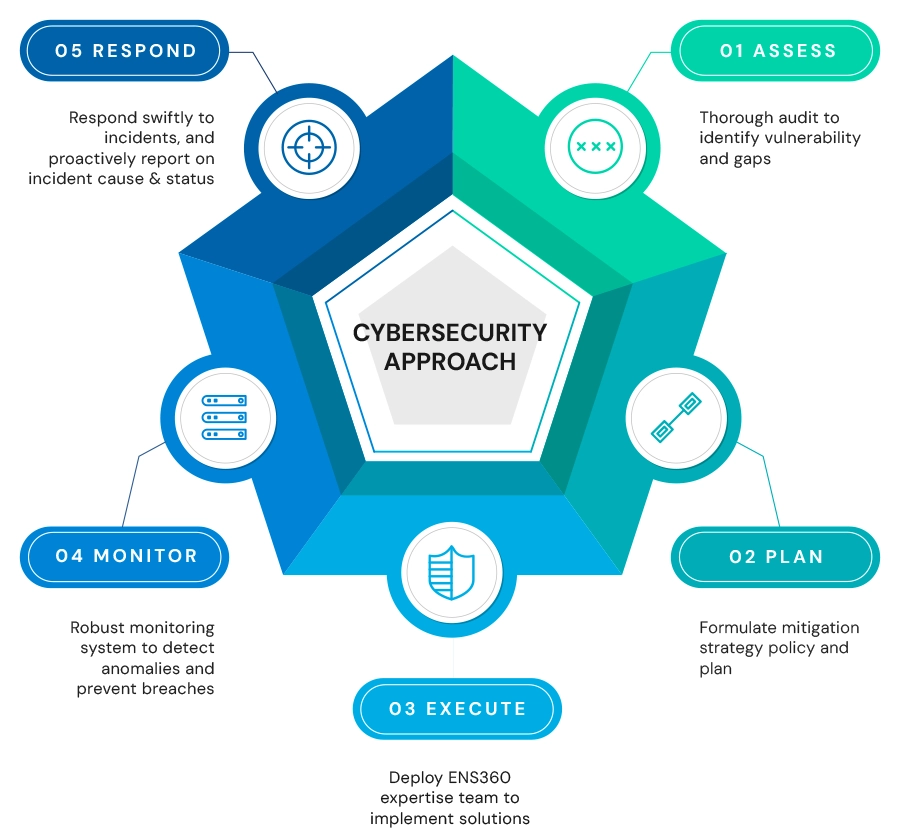
Best Cyber Security Consulting and Approach
Entrust Network provides a full suite solution (ENS360) of cyber security services and solutions for small to medium enterprises (SMEs) across all industries.
1. ASSESS
Conduct a thorough audit to identify cyber security vulnerabilities and compliance gaps, assessing the risk exposure for a comprehensive understanding of potential threats and determine the likelihood of vulnerabilities being exploited.
2. PLAN
Formulate a strategy to mitigate cyber security risks identified in the audit, including infrastructure and software implementation, policy development, and a plan for cyber security awareness and training initiatives.
3. EXECUTE
Deploy our ENS360 Singapore cyber security team to implement pragmatic solutions, ensuring seamless deployment of security measures within allocated resources and budget.
4. MONITOR
Establish robust monitoring systems to identify cyber security anomalies, proactively preventing breaches and enhancing the cybersecurity framework through continuous monitoring. All changes to system and operational environment will be documented.
5. RESPOND / REPORT
Swiftly respond to and recover from cybersecurity incidents, evaluating the effectiveness of the recovery plan upon execution, and maintaining ongoing visibility into your cybersecurity status through regular checks and reports.
Expert insights on key cyber security statistics show that:
Diverse Talent & Perspectives
Diverse Talent & Perspectives
Diverse Talent & Perspectives
TESTIMONIAL
Part of our team.
“Entrust Network offers comprehensive IT support for our offices and food and beverage outlets across all Changi Airport Terminals. Their team specializes in cloud computing and cybersecurity, consistently providing excellent assistance to our end users. By integrating seamlessly with our operations, they demonstrate exceptional responsibility and responsiveness, ensuring our IT needs are met efficiently and effectively.”

Dalton Huskins, Digital & Technology Director APAC
SSP Group Plc
Dalton studied cybersecurity and forensics in Manchester, UK. With nine years of experience in the technology industry, he has spent the last eight years at SSP Group PLC, where he currently leads the Digital & Technology department. In this role, he develops comprehensive technology strategies and drives digital transformation by deploying enterprise-level solutions across the Asia Pacific region.

RELATED TECHNOLOGY ARTICLES
Featured Insights On Technology
How Your Business Can Benefit From Cyber Security Consulting Services
Leveraging Threat Intelligence to Elevate Endpoint Security
What is next-gen firewall (NGFW) and why companies need it?
PROTECT & GROW YOUR BUSINESS
Optimised security across your organisation
Get an assessment of your current security posture by reaching out to our team to identify your immediate gaps and challenges.


