

This article outlines key information regarding the Personal Data Protection Act (PDPA) and presents a comprehensive action plan for ensuring compliance. The recommendations are tailored for Small and Medium Enterprises (SMEs).
1. What is the mandatory requirement by PDPC?
All companies registered in Singapore are required to appoint a Data Protection Officer (DPO) and ensure that their business contact information is publicly accessible by 30 September 2024.
2. How do I update the DPO contact via Bizfile + (ACRA)?
To update your DPO contact, please use Microsoft Edge or Google Chrome, as Mozilla Firefox is not fully compatible with the above mentioned websites.
For organisations registered with ACRA, please register/ update your DPO info via https://www.bizfile.gov.sg
On the top menu, go to eServices > Others > Register/ Update Data Protection Officer(s).


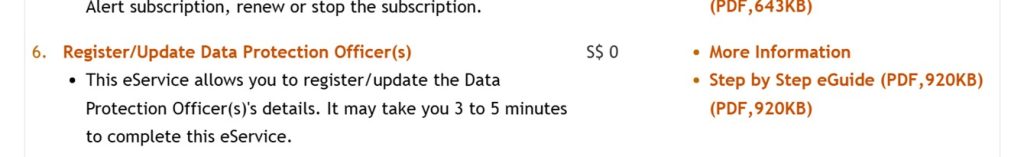

Please note that the right Corppass access is required to update DPO information.
Follow the steps on the website to register.
3. Are there any qualification requirements for a DPO?
The appointed Data Protection Officer (DPO) should be a senior member of the organisation. In many Small and Medium Enterprises (SMEs), I.T. or H.R. managers are often assigned this role, as they are typically responsible for handling and processing personal data.
Given the significant responsibilities of a DPO, we recommend that the appointed individual be well versed in PDPA regulations and proficient in data protection policies, as well as fundamental cybersecurity controls.
I have personally attended the PDPA course conducted by Singapore Management University (SMU) and highly recommend it for all appointed DPOs. The three-day course, led by Celine Chew, was insightful and professionally delivered. Her expertise made the course highly valuable, and the seminar environment was both conducive and comfortable for learning.
We recommend that you attend and take the certification exam to ensure formal recognition as a certified DPO.
For more information, please access the website link here.
4. What must a DPO do?
1. Conduct a Data Inventory
2. Implement Security Measures
3. Setup I.T. Policies
4. Conduct Staff Training
5. Handle cyber incident and report to PDPC
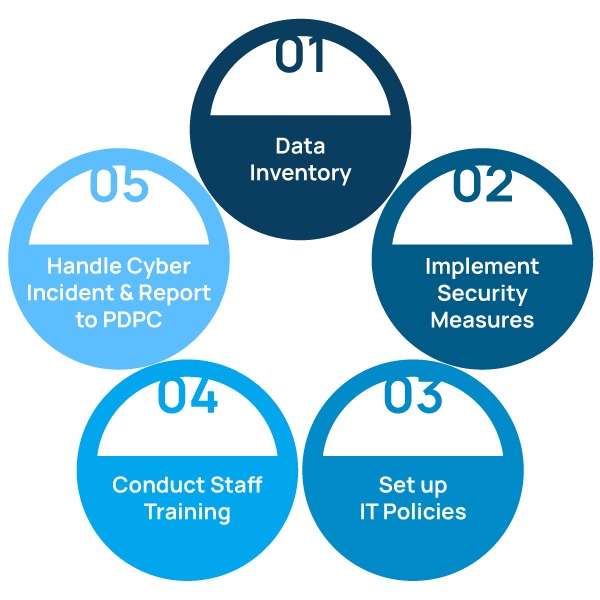

This process is not a one-time effort but rather a continuous cycle. Regular reviews and updates of the data inventory, security measures, I.T. policies, and staff training are essential to adapting to new threats, regulatory changes, and technological advancements.
Step 1 – Data Inventory
To protect personal data effectively, the first step is to conduct a comprehensive inventory of all personal data within the organisation.
This data may exist in various forms, including physical (hard copy), digital (soft copy), databases, and backups. It could be stored in different locations, such as on-premises servers, cloud-based platforms, or with third-party hosting providers and/or data shared with external data intermediaries.
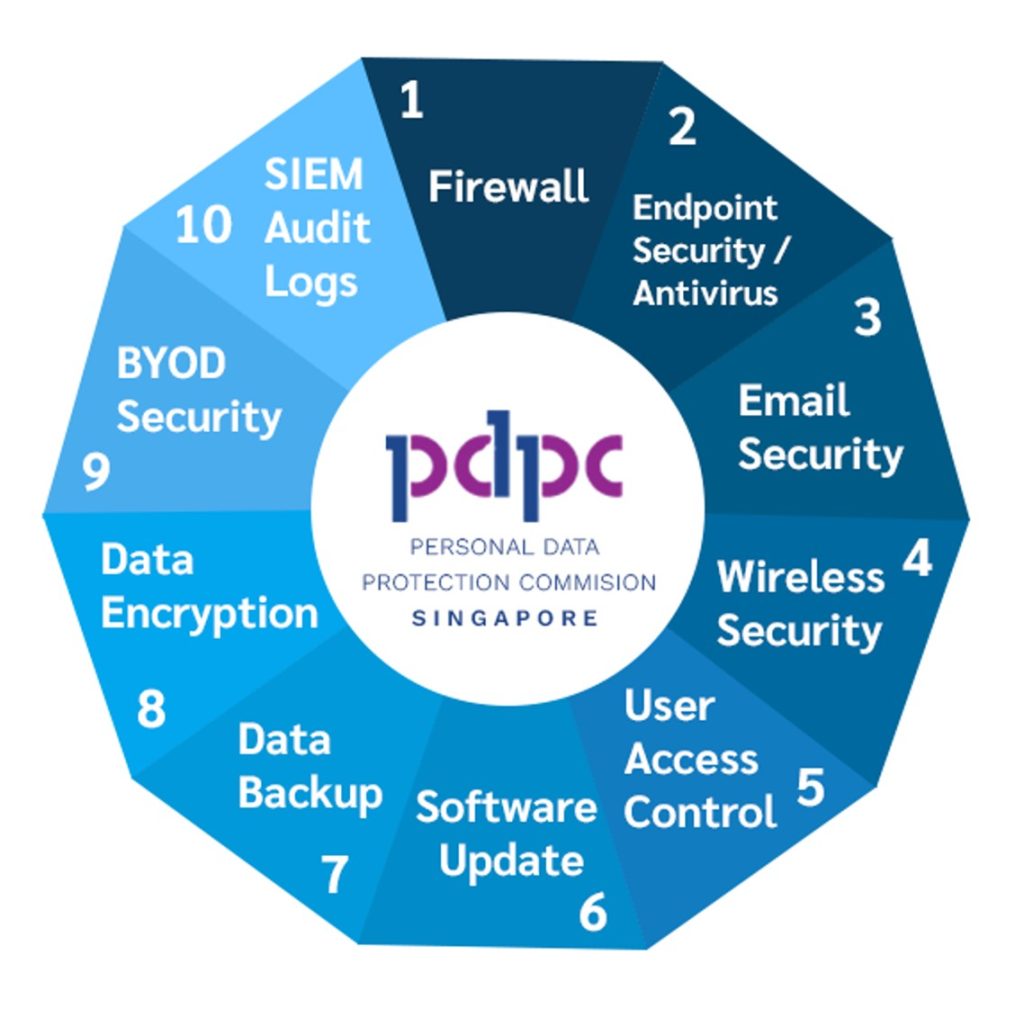
Step 2 – Implement Security Measures
PDPC recommends the following technical measures as shown below. Based on our professional experience, we consider measures 1 through 7 to be critical and essential for ensuring compliance with the Personal Data Protection Act (PDPA). These measures should be prioritised in your data protection strategy.

Step 3 – Setup I.T. Policies
IT policies must be established, formally endorsed and approved by management, and communicated clearly to all staff members for effective implementation.
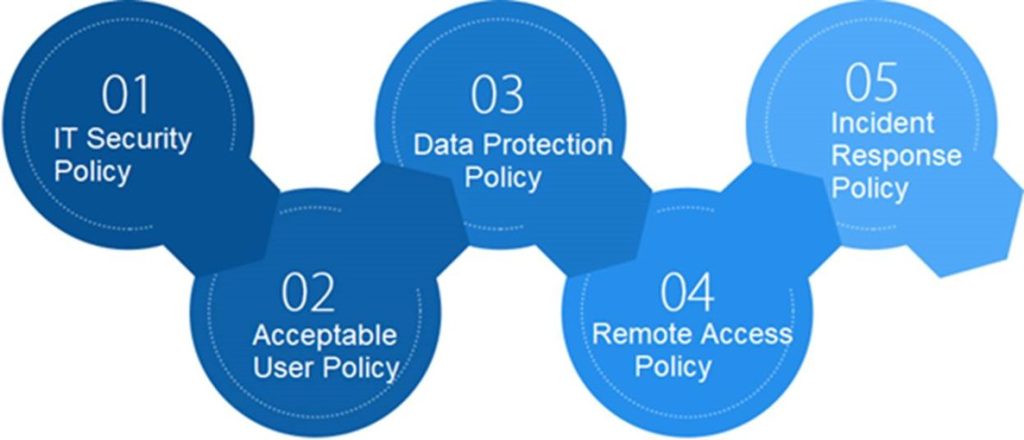

5 Essential IT Policies are,
3a – IT Security Policy
An IT Security Policy outlines the rules and procedures governing the access and use of an organisation’s IT assets and resources by all individuals.
3b – Acceptable use policy
An Acceptable Use Policy (AUP) stipulates the constraints and practices that users must adhere to when accessing the corporate network or the internet.
For example:
- Corporate email accounts must be used strictly for business purposes.
- Downloading movies or engaging in other non-business activities using the office internet is strictly prohibited.
3c – Data Protection Policy
A Data Protection Policy outlines the organisation’s commitment to protecting personal data and procedures for how personal data is collected, stored, and used in compliance with PDPA.
3d– Remote Access Policy
The Remote Access Policy specifies the acceptable methods for remotely connecting to the organisation’s internal network.
3e – Incident Response Policy
This policy defines the roles, responsibilities, and procedures for responding to security incidents swiftly and effectively.
Step 4 – Conduct Staff training on Cybersecurity and data protection
- Regularly share news on the latest scams and cyberattacks to all staff
- Conduct e-learning programs, quizzes and interactive games focused on data protection
- Launch phishing simulation campaigns to enhance staff awareness and vigilance regarding cybersecurity.
5. What actions should a DPO take in the event of a cyber-attack or data breach?
- For personal data loss of 500 or more, you are required to report to PDPC.
- For financial loss and criminal activity, you are required to report to the police and relevant financial institutions.
- For advanced persistent threats (APTs) or national security threats, do not hesitate to contact the Cyber Security Agency (CSA) for assistance.
Here is the list of useful links:
https://www.police.gov.sg/Advisories/Crime/Cybercrime/Ransomware
https://go.gov.sg/singcert-incident-reporting-form
https://eservice.pdpc.gov.sg/case/db
https://www.csa.gov.sg/reporting
Notify the client or supplier involved
If your organisation experiences an attack, notify your customers, clients, suppliers, as well as staff and employees, so they can take appropriate measures to protect themselves. Your legal team or service provider may assist in facilitating the notification process.
Reporting to Authorities
Organisations may need to assume that data could have been exfiltrated if the threat actor successfully accessed your infrastructure or systems.
DPO must report to the police if criminal activity (e.g., hacking, theft, or unauthorized system access by an employee) is suspected and to preserve evidence for investigation.
Organisations should assume that data may have been exfiltrated if a threat actor has successfully accessed your infrastructure or systems.
The Data Protection Officer (DPO) must report any suspected criminal activity, such as hacking, theft, or unauthorized access by an employee, to the police. It is also crucial to preserve all relevant evidence for subsequent investigation.
Lim Jamson is the author of the article.
Jamson is a technopreneur with a strong passion for cloud computing and cybersecurity. He holds a master’s degree in computing from the National University of Singapore (NUS). Additionally, he is a Certified Ethical Hacker and a Practitioner in Personal Data Protection.
DPO as a Service.
If your company plans to outsource the DPO appointment, Entrust Network offers DPO as a Service, from consultation to implementation and ongoing support,
Our DPO service ensures your data management practices are secure and aligned with legal standards.
Select the plan that fits your requirements and protect your data with confidence.


